Exploring Secure S3 Bucket Creation with Terraform: With and Without AWS Key Management Service (KMS)
Introduction:
In today's data-driven world, secure storage and encryption are of paramount importance. Amazon S3 (Simple Storage Service) is a popular cloud storage solution, and with the added security provided by AWS Key Management Service (KMS), you can ensure your data remains protected. In this blog, we will dive into the process of creating an S3 bucket both with and without KMS encryption using Terraform. Additionally, we'll explore the features of AWS KMS and discuss the advantages of leveraging KMS for enhanced data security.
Creating an S3 Bucket without KMS Encryption:
Before we explore KMS encryption, let's start by understanding the basic process of creating an S3 bucket using Terraform without enabling KMS encryption.
The following Terraform code snippet demonstrates this:
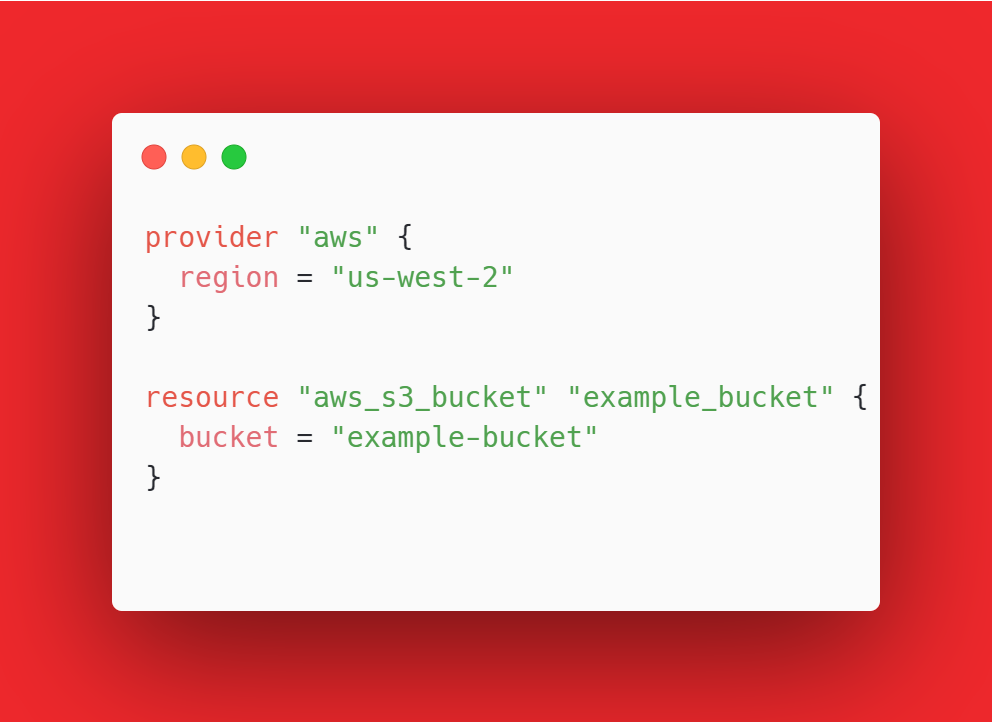
In the above code, we specify the AWS provider region and define an S3 bucket resource. Running Terraform with this code will create an S3 bucket without any additional encryption features.
Creating an S3 Bucket with KMS Encryption:
To enhance the security of our S3 bucket, we can utilize AWS Key Management Service (KMS) for server-side encryption.
Let's modify the previous Terraform code to include KMS encryption:

In this updated code, we introduce the server_side_encryption_configuration block to enable server-side encryption. The apply_server_side_encryption_by_default block specifies the default encryption settings, with sse_algorithm set to "aws:kms". You'll need to provide the KMS key ID or alias using kms_master_key_id parameter.
Manually Creating a KMS Key or Alias: To manually create a KMS key or alias, follow these steps:
Step 1: Sign in to the AWS Management Console.
Step 2: Open the AWS Key Management Service (KMS) console.

Step 3: Navigate to the "Customer managed keys" section.

Step 4: Click on the "Create key" button.
Step 5: Configure the key settings, such as key type, key material origin, and key usage permissions. You can choose to enable rotation for added security.
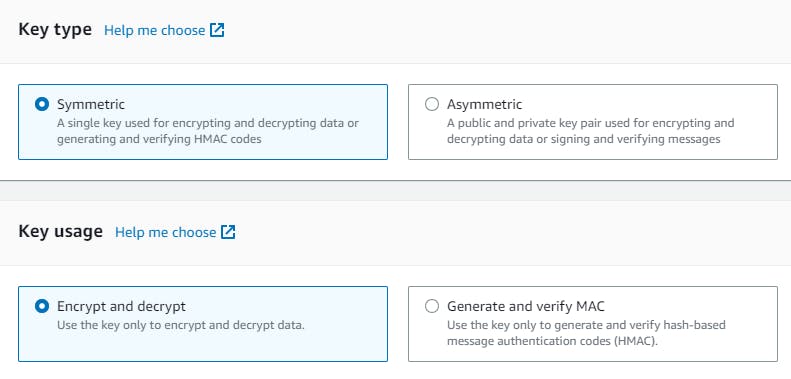
Step 6: Provide a key alias to easily reference the key in your Terraform code and applications. The alias should be unique and descriptive.

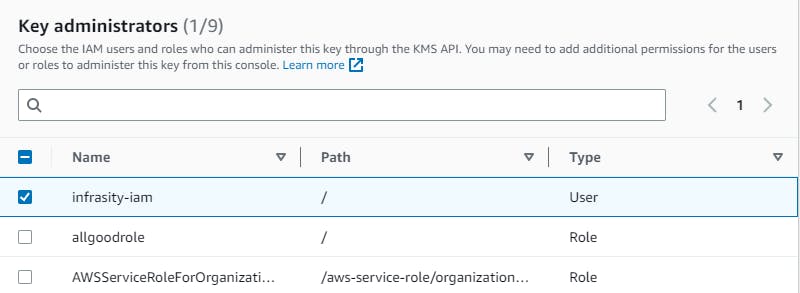

Step 7: Review the key settings and click on the "Create key" button to create the KMS key.
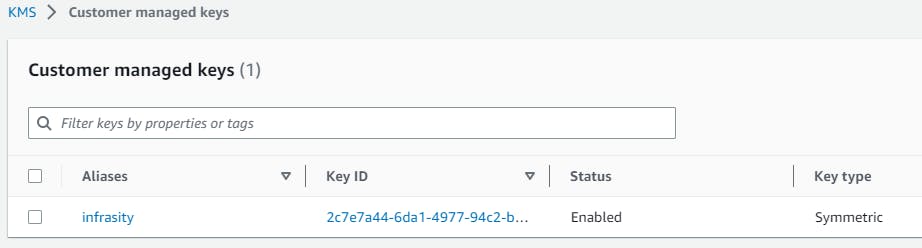
Once the KMS key or alias is created, you can use its ID or alias in the Terraform code snippet mentioned earlier by replacing the "alias/aws/s3" placeholder.
Using KMS Encryption vs. Not Using KMS Encryption:
When you choose to use KMS encryption for your S3 bucket, several important differences come into play compared to not using KMS encryption:
Enhanced Data Security: By utilizing KMS encryption, your data is protected with an additional layer of security. The encryption keys are managed securely by AWS KMS, reducing the risk of unauthorized access to your data.
Fine-Grained Access Control: KMS allows you to define fine-grained access policies, granting specific permissions to individuals or roles for using encryption keys. This ensures that only authorized entities can access and decrypt the data.
Compliance and Auditability: KMS provides detailed logs that enable you to track key usage and meet compliance requirements. You can easily demonstrate data encryption and compliance to auditors.
Key Rotation and Management: KMS supports key rotation, allowing you to regularly update encryption keys without disruption. Key management tasks, such as key creation, deletion, and rotation, are handled by KMS, simplifying the process for you.
Seamless Integration: KMS integrates seamlessly with other AWS services, including S3, EBS, RDS, and more. This allows for transparent encryption and decryption of data within your applications and AWS infrastructure.
Advantages of Using KMS for S3 Bucket Encryption:
By leveraging AWS KMS for S3 bucket encryption, you can enjoy several advantages:
Enhanced Data Protection: KMS ensures that your data remains encrypted at rest, providing an additional layer of security against unauthorized access.
Simplified Key Management: KMS handles the complexity of key management, making it easier to implement and maintain encryption across multiple services and accounts.
Compliance and Auditability: KMS helps you meet regulatory compliance requirements by providing a secure and auditable key management system.
Seamless Integration: KMS integrates seamlessly with other AWS services, allowing you to encrypt and decrypt data transparently within your applications.
Conclusion:
In this blog, we explored the process of creating an S3 bucket with and without AWS Key Management Service (KMS) encryption using Terraform. We discussed the features of AWS KMS and highlighted the advantages of using KMS for S3 bucket encryption. By leveraging KMS, you can ensure the confidentiality and integrity of your data, meeting security requirements and maintaining compliance. Whether you choose to enable KMS encryption or not, Terraform simplifies the provisioning and management of S3 buckets, making it an efficient tool for securing your cloud storage infrastructure.